Miners in China have begun to cross their fingers and look over there shoulders as continued reports of dangerous viruses that look to extradite money have increased.
First detected in August 2018, the ransomware, known as ‘hAnt’, has been targeting specific mining rigs such as the

In perhaps an even more worrying tale, the ransomware gives two choices: pay ten Bitcoin or spread the code. Otherwise, it will turn off the fan causing overheating and therefore the destruction of the machine.
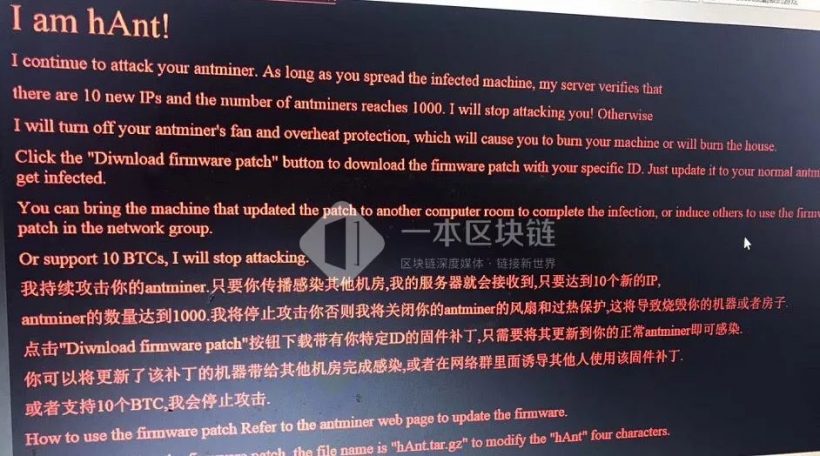
The message reads in English:
“I am hAnt! I continue to attack your Antminer. As long as you spread the infected machine, my server verifies that there are 10 new IPs and the number of
antmiAners reaches 1,000. I will stop attacking you! Otherwise, I will turn off yourantminer’s fan and overheat protection, which will cause you to burn your machine or will burn the house.Click the ‘Download firmware patch’ button to download the firmware patch with your specific ID. Just update it to your normal Antminer to get infected.You can bring the machine that updated the patch to another computer room to complete the infection or induce others to use the firmware patch in the network group.
Or support 10 BTCs, I will stop attacking.”
Hacker’s virus message
The message is accompanied by a picture akin to a Prodigy album cover, with an ant next to two pickaxes and green ASCII characters, like the red skull screen displayed by the NotPetya ransomware.
Security experts in China believe ‘hAnt’ comes hidden inside tainted versions of mining rig firmware that has been present online since mid-2018, but no clear source of origin is clear. They have looked to remind users that they should improve their network security awareness, open the system to automatically update, have a timely patch, avoid the use of weak passwords in order to not give the criminals a chance.
The main solution and perhaps the only one available has been to put in clean firmware and re-flash the infected mining equipment’s SD card. Users are also being advised to download the firmware directly from the original manufacturer of the rigs and not other download sites.
This week, according to a report from the Xinhua News Agency, the Ruixing Company recently released the “2018 China Cyber Security Report” which stated that their “cloud security” system intercepted a total of 77.86 million virus samples as the total number of viruses surged 55.63%. Many criminals have begun targeting the cryptocurrency field according to the analysis from the report.
This has to be worrying for Bitmain and other miners across the Middle Kingdom, let’s hope that there is a fix to the problem and the criminals are caught!